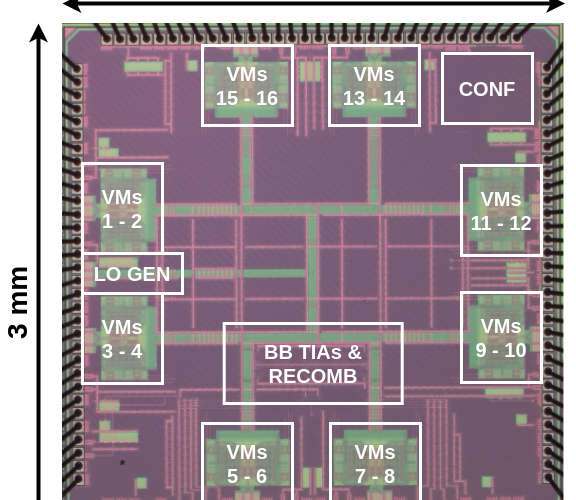
Overview
Security plays a crucial role in the design of low-power connected sensors and edge devices. The potential threats to intelligent wireless systems are particularly hazardous due to the sensitive nature of the exchanged data. Given the stringent constraints on energy and computation resources, relying solely on cryptographic mechanisms for device security is not sufficient. To bolster the security of intelligent sensing and communication systems, our approach is to: (1) identify security vulnerabilities in intelligent sensors; (2) develop innovative countermeasures that leverage the distinctive characteristics of the physical layer; (3) provide tangible demonstrations of these solutions in energy-efficient integrated hardware systems; and (4) analyze performance trade-offs associated with embedding security in integrated intelligent sensor hardware.
Energy- and Spectrally-Efficient Wireless Systems Embedding Security:
Collaborators:
Prof. Yonina Eldar – Weizmann Institute of Science, Prof. Nir Shlezinger – Ben-Gurion University of the Negev, Dr. Lei Poo – Analog Devices, Dr. Tao Yu – Analog Devices, Dr. Benoit Dufort – Analog Devices
Funding: Semiconductor Research Corporation, Analog Devices (ADI)
Team: Timur Zirtiloglu (Lead RF Integrated Circuit Designer), Arman Tan, Arslan Riaz, Alperen Yasar (Lead Secure Integrated Circuit Designer), Eyyup Tasci (Visiting Undergraduate Researcher), Peter Crary
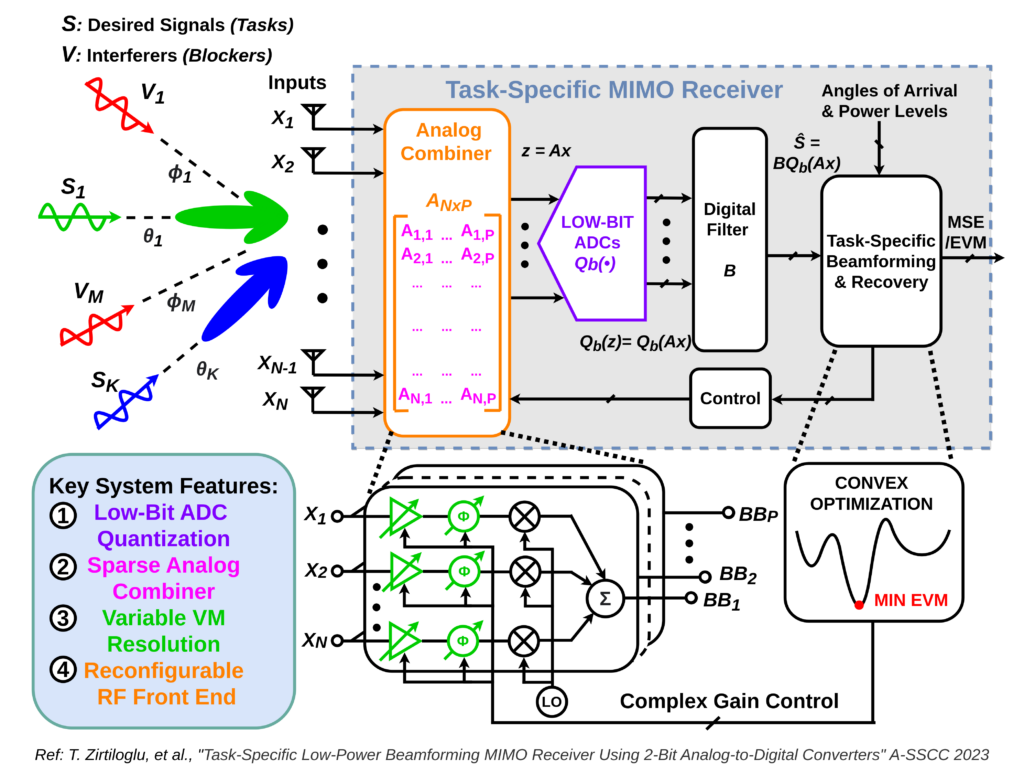
Traditional radio-frequency (RF) systems employ brute-force data acquisition through high-resolution quantization and Nyquist sampling rates, resulting in elevated power consumption and hardware design complexity. To address these challenges, we advocate for the integration of information-centric algorithms in the design of agile RF receivers. This approach aims to achieve heightened spectrum utilization while minimizing energy consumption, thereby mitigating the overhead of embedding security measures in the physical layer. It is crucial to tackle security concerns at the physical-layer-design level rather than treating them as an afterthought in software or digital algorithms, especially for future sensing and communication systems.
The attack surface at the physical layer can exploit hardware vulnerabilities through side-channel attacks and fundamental RF/analog signal and channel parameters. To establish secure analog/RF circuits and wireless sensing systems, understanding and analyzing these vulnerabilities using universal metrics are essential. Mitigating these vulnerabilities requires the development of hardware-algorithmic techniques that leverage the unique characteristics of the physical layer and integrated circuit components for security. Choosing appropriate security protocols and RF/analog security primitives necessitates a systematic study of performance trade-offs, considering factors such as energy consumption, latency, and area implications, especially in tightly constrained systems.
Publications:
Tutorials:
GRAND-EDGE:
Collaborators:
Prof. Muriel Médard – MIT EECS, Prof. Ken Duffy – Northeastern University ECE, Prof. David Starobinski – BU ECE
Funding: NSF SWIFT, DARPA
Team: Dr. Furkan Ercan (Lead Designer), Kevin Galligan (Ken Duffy’s Ph.D. student)
The presence of random jammers, capable of overpowering transmitted signals, presents a practical challenge for various wireless communication protocols. Consequently, wireless receivers must adeptly manage both standard channel noise and deliberate or unintentional jamming. Addressing this challenge, we proposed an innovative method to bolster the resilience of the recent family of universal error-correcting GRAND algorithms. This approach, named Erasure Decoding by Gaussian Elimination (EDGE), specifically influences the syndrome check block and is applicable to any GRAND variant. Our simulations demonstrated that the EDGE variants markedly diminish both the Block Error Rate (BLER) and computational complexity by up to five orders of magnitude when compared to the original GRAND and ORBGRAND algorithms.
Publications:
Security Strategy for Soft Decoding Against Smart Bursty Jammers:
Collaborators:
Prof. Muriel Médard – MIT EECS, Prof. Ken Duffy – Northeastern University ECE, Prof. David Starobinski – BU ECE
Funding: NSF SWIFT, DARPA
Team: Dr. Furkan Ercan (Lead Designer), Kevin Galligan (Ken Duffy’s Ph.D. student)
Jamming attacks pose a threat to wireless communication, potentially causing significant disruptions or complete denial of service (DoS). Detecting these attacks is challenging due to the growing sophistication of jamming devices. While forward error correction is commonly used to mitigate channel noise, it becomes less reliable in the presence of jammers, leading to a decline in error correction performance. Bursty jammers have a more pronounced impact than non-bursty ones, as traditional decoders assume independent noise occurrence for each bit.
However, we propose a solution leveraging temporal dependencies to identify jammed bits, introducing a pre-decoding step that updates log-likelihood ratio (LLR) reliability information without modifying the decoding algorithm. Our method enhances decoding performance, accurately detecting a significant proportion of jamming in received frames. Applied to specific decoding algorithms like ORBGRAND, our approach reduces the block-error rate (BLER) by an order of magnitude for selected codes, preventing a complete DoS at the receiver.